What is DNS hijacking? How to detect & prevent it

The Domain Name System (DNS) is often referred to as the “phone book of the internet.” It translates human-friendly domain names (like example.com) into numeric IP addresses that computers and networks understand. Every time you browse a website or launch an online application, multiple DNS queries are executed in the background. The accuracy and security of this process are key, not just for convenience but for ensuring a safe online experience.
Yet, it’s this foundational aspect of DNS that makes it vulnerable. If attackers manage to intercept or alter DNS records, they can redirect users to fraudulent websites, capture logins and passwords, access sensitive emails, bypass security protocols, or even steal funds. This threat is known as DNS hijacking, impacting private users as well as major corporations, government agencies, and financial institutions. According to IDC research published by Cloudflare, 87% of organizations worldwide faced DNS attacks in the past year, with 76% experiencing service outages and downtime affecting critical systems. On average, resolving these attacks takes over 5.5 hours, leading to significant financial and reputational damage.
DNS hijacking is especially concerning for fintech and Web3 projects. This CertiK report for Q2 2025 noted losses exceeding $801 million from various attacks, a large portion attributed to phishing and DNS spoofing. In some instances, victims unknowingly entered their seed phrases or logins on counterfeit websites created through DNS compromises.
Thus, DNS hijacking is a genuine and widespread threat affecting millions of users and countless companies. We’ll break down how DNS hijacking works, how it differs from other attacks, how to detect it, and the measures that can help safeguard against it.
What is DNS hijacking
DNS hijacking is an attack where an attacker takes control of the Domain Name System (DNS), redirecting user requests to malicious or fraudulent IP addresses. This means that when a user types in a familiar URL (i.e. bank.com) they may end up on a fake site that closely mimics the original.
The main goals of the attack are:
- stealing credentials (logins, passwords, seed phrases, card numbers);
- intercepting and manipulating traffic, therefore gaining access to sensitive data exchanged online;
- spreading malware and distributing harmful software to unsuspecting users;
- bypassing security filters and censorship tools.
Difference from related attacks
DNS spoofing, or DNS cache poisoning, occurs at intermediate nodes or within the resolver cache. Here, the attacker injects a false DNS response, which gets stored in a computer’s or server’s cache. The impact is typically local and short-lived, redirecting users until the cache refreshes.
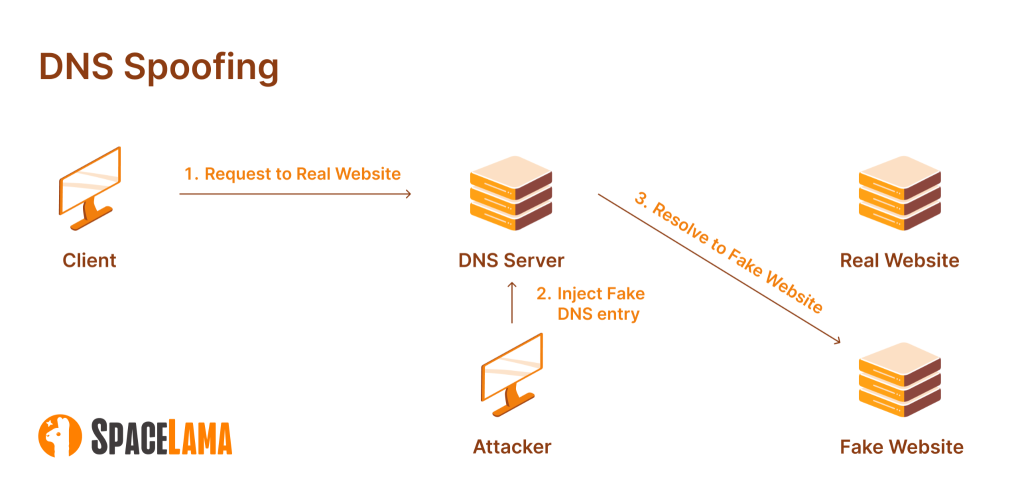
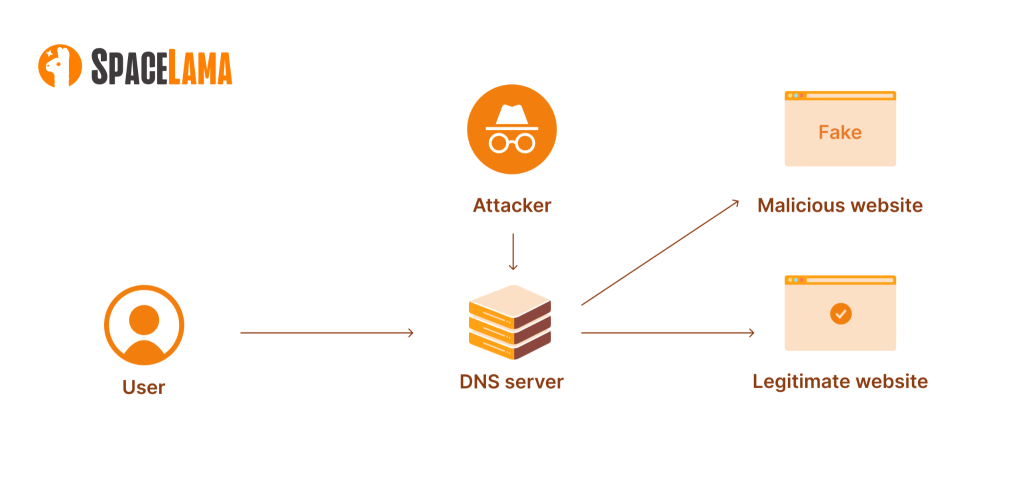
DNS hijacking, in contrast, targets the authoritative sources of DNS records, such as registrars, DNS providers, or even network routers. This allows for systematic user redirection on a large scale, lasting as long as the attacker maintains control over the records.
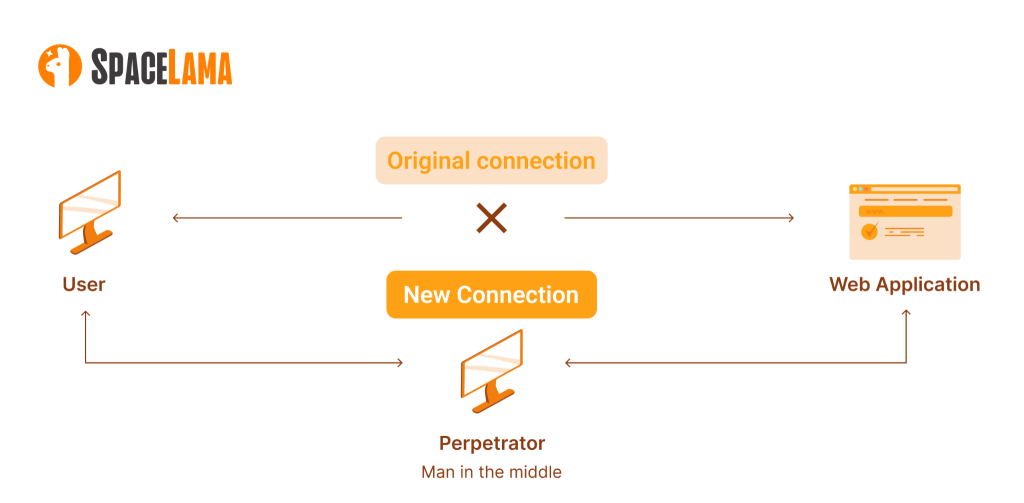
Man-in-the-Middle (MITM) attacks represent a broader category where an attacker positions themselves between the user and the server, intercepting or modifying data in transit. DNS hijacking can be a facet of an MITM attack; however, MITM encompasses more than just DNS manipulation and can impact various layers of network communication.
While spoofing or poisoning typically affects only a local cache or a single ISP, hijacking poses a threat to entire segments of the internet. For instance, Cloudflare has documented global campaigns where compromised DNS providers redirected traffic from government and financial organizations to websites controlled by attackers.
DNS hijacking mechanisms and scenarios
High-level attack overview
- Initial access. The attacker gains authentication access with the domain registrar, DNS provider, or a compromised resolver. This can be achieved by stealing credentials, API keys, or access to control panels.
- DNS record alteration. They modify the DNS records, such as A, CNAME, NS, MX, and redirect traffic to malicious servers they control.
- Deployment of fake sites. A cloned website or phishing page is set up on the malicious server, often with a forged TLS/SSL certificate to bypass browser security warnings.
- User redirection. Users are silently sent to the fake site, unknowingly entering their login credentials, seed phrases, or payment information, all of which are captured by the attacker.
- Escalation of attack. Over time, the attacker may escalate the operation, spoofing APIs, altering smart contract addresses in Web3 interfaces, or injecting scripts to drain funds.
How DNS hijacking works
DNS attacks often start with the theft of a domain administrator’s credentials or unauthorized access to the DNS management panel—typically through phishing campaigns or leaked passwords. Once attackers gain access, they alter critical DNS records (such as A, CNAME, or NS) to redirect the domain to a server they control.
In some cases, the compromise occurs not on the administrator’s end but within the registrar’s or DNS provider’s infrastructure, allowing attackers to target thousands of domains simultaneously. On home networks, a simpler scenario often unfolds when an attacker compromises a router and modifies its DNS settings, resulting in all devices on that network being redirected to malicious sites.
In cryptocurrency projects, attackers frequently exploit this method to replace smart contract addresses on fake decentralized application (dApp) interfaces, tricking users into signing transactions that funnel funds directly to attacker-controlled wallets.
Such attacks can be challenging to detect. Attackers often redirect only a portion of traffic or conduct limited “test” hijacks to avoid triggering security alerts and delaying discovery.
How to detect DNS hijacking
1. Signs on the user side
A user may suspect DNS hijacking if:
- a website is loading but something looks kinda off, i.e. the design or logos are different, a familiar piece of content is missing;
- their browser shows a certificate warning (“Your connection is not secure”) on a site that has never triggered such alerts before;
- pages load unusually slowly or unexpectedly redirect to other domains;
- pop-up ads or banners appear on websites where they normally wouldn’t (now that’s a common sign of local malware or router hijacking);
- email suddenly stops working (MX records may have been changed and messages could be delivered to the attacker).
Tip. If something seems off, avoid entering passwords or payment details. First, verify the domain name and check the SSL/TLS certificate.
2. Manually checking DNS records
If you’re a domain administrator or suspect a DNS issue, start by running these basic commands:
- dig example.com A +trace
- dig example.com NS
- dig example.com MX
- nslookup example.com
Compare the output with the reference records stored in your registrar’s or DNS provider’s control panel. Any unexpected changes should raise a red flag. Cloudflare and Fortinet recommend keeping a regularly updated “golden copy” of your DNS configuration for quick comparisons during incidents.
3. Real-time monitoring
Utilize DNS change monitoring services like SecurityTrails, DNS Spy, Intruder, or Detectify. These tools should alert you whenever DNS records are modified.
Enable registrar notifications via email or SMS for any changes to name servers or domain contact information. Additionally, review access logs for your domain management panel. Unrecognized IP addresses or login attempts should trigger an immediate password reset and the activation of two-factor authentication.
4. Check your router and local DNS
Routers are a common target for hijacking attacks.
Routers are often prime targets for hijacking attacks.
Log in to your router’s web interface and review the configured DNS servers. These should typically be your ISP’s addresses or well-known public resolvers, like Cloudflare (1.1.1.1) or Google (8.8.8.8). If you notice an unknown IP address, your router may have been compromised.
To secure it, reset the router to factory settings and update its firmware to eliminate any malicious configurations.
5. Compare responses from third-party resolvers
To verify whether the issue is local, perform the following checks:
- dig example.com A @1.1.1.1 # Cloudflare
- dig example.com A @8.8.8.8 # Google
Compare these responses with those from your local resolver. If the results differ, this strongly indicates that your DNS traffic might be spoofed or hijacked.
6. Automated solutions
SpaceLama reminds you that for large organizations, automated monitoring is a must.
- SIEM systems. Use solutions like Splunk to detect suspicious DNS log changes in real time.
- Threat intelligence feeds. These can alert you to known domain compromises or ongoing global attacks.
- DNSSEC validation. Enable DNSSEC on your resolvers and domains to cryptographically verify DNS responses and block spoofed records (when supported on both ends).
How to protect yourself from DNS hijacking
The potential consequences of DNS hijacking can be devastating, leading to identity theft, data breaches, and financial loss. Fortunately, there are proactive steps you can take to safeguard yourself and your organization. By adopting these best practices, you can significantly reduce your vulnerability to DNS hijacking and enhance your overall online security.
Secure your registrar and DNS provider accounts
- Enable two-factor authentication (2FA) for every account with access to your domain or DNS management panel. This blocks the majority of credential-based attacks.
- Use strong, unique passwords and rotate them regularly.
- Limit administrator privileges. Grant read-only access to anyone who does not need to modify DNS records.
- Turn on change notifications in your registrar panel so you receive alerts for any updates to DNS records or contact information.
Technical measures at the DNS level
- Implement DNSSEC. It cryptographically signs DNS records, allowing resolvers to verify that responses are authentic and have not been tampered with.
- Use registry lock or similar domain-locking services, as this “freezes” critical records (NS, A, CNAME) and requires out-of-band verification before any changes are applied.
- Monitor for DNS changes using third-party services (e.g., SecurityTrails, DNS Spy, Intruder, Detectify) or your provider’s built-in monitoring features.
- Maintain a golden configuration file listing all critical records (A, AAAA, CNAME, MX, TXT) so you can quickly verify and restore them if compromised.
Router and LAN security
- Change default router passwords and update firmware.
- Change default router passwords and update firmware regularly.
- Verify which DNS servers are configured. Stick to trusted resolvers such as Cloudflare (1.1.1.1), Google (8.8.8.8), or your ISP’s official servers.
- Disable remote administration unless you absolutely need it.
- Use a VPN on public Wi-Fi networks to prevent DNS traffic interception, especially when DNSSEC validation is unavailable.
Business and DevOps practices
- Centralize management and logging. Keep domains, DNS, hosting, and SSL certificates under a single management system with audit logs.
- Regularly audit subdomains for takeover risks, especially those pointing to external services such as AWS S3, Heroku, or GitHub Pages.
- Conduct security testing and pentests. Simulate DNS hijacking scenarios to identify weaknesses before attackers do.
- Create and maintain an Incident Response Plan (IRP), documenting step-by-step actions for restoring DNS records, communicating with users, and mitigating damage if an attack occurs.
Redundancy and fault tolerance
- Use multiple DNS providers (multi-DNS) to reduce the risk of a single point of failure or full takeover.
- Configure secondary/backup name servers and keep them synchronized via API or automation tools.
- Leverage a CDN with built-in DNS protection (e.g., Cloudflare DNS, Akamai) for critical services — these platforms can monitor anomalies and block suspicious record changes automatically.
DNS hijacking is a pressing threat to the internet’s stability. When attackers compromise DNS records, they can easily redirect you to counterfeit websites, steal your credentials, intercept emails, and even drain your crypto wallets.
The good news? Many attacks can be prevented. Implementing two-factor authentication, DNSSEC, registry locks, and constant monitoring can significantly reduce your risk. But remember, no defense is flawless. Human error and provider vulnerabilities will persist no matter what.
That’s why choosing a safe domain and hosting provider is critically important. So, choose SpaceLama. With robust security features, SpaceLama helps safeguard against DNS hijacking, keeping your online assets secure.
The stakes are high. Don’t let your guard down. Start using SpaceLama today.