How to protect yourself from domain hijacking

A domain name is an invaluable asset for your company. It serves as a brand ambassador, a channel for customer engagement, a source of trust, and a revenue generator. Losing control of a domain can lead to serious consequences, ranging from reputational damage to financial losses, legal disputes, and service outages.
In 2024, experts discovered nearly 800,000 domains with improperly configured DNS records. These domains pointed to inactive or unowned servers, making them easy targets for exploitation. Such domains are dubbed “sitting ducks”. They appear registered but lack proper protection. Approximately 70,000 of these (9%) have already been hijacked by attackers for phishing, spam, and other malicious activities.
Those who overlook DNS settings, fail to implement security measures at their registrars, or leave domains unrenewed and unmonitored are particularly vulnerable. With so much at stake, let’s safeguard your website from hijacking.
How domain hijacking works
Domain hijacking occurs when an attacker gains unauthorized control of your domain name. Think of it as the digital equivalent of real estate theft: the “address” still technically exists, but now it’s owned by someone else.
Main attack methods
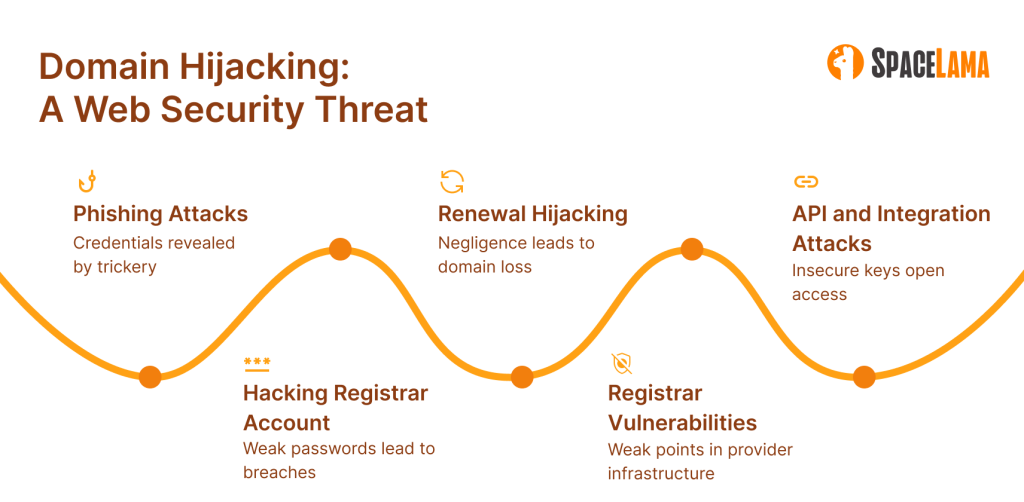
Phishing and social engineering
One of the most common scenarios involves an attacker tricking a domain owner or administrator into revealing registrar credentials. This could take the form of a fake email claiming to be from support, asking for password confirmation, or an SMS with a link to a fraudulent website. With just one click, the attacker can gain access to the domain.
In July 2023, the Japanese CERT (JPCERT/CC) confirmed a case where a domain was stolen following a phishing attack. The domain administrator was redirected to a counterfeit website, resulting in the unauthorized transfer of the domain to another registrar.
Hacking a registrar account
If a domain owner uses a weak password or reuses the same password across various services, a hacker can often guess it or purchase it on the dark web. Once they log into the account, they can change DNS records or transfer the domain to another registrar.
For instance, in 2008 a popular US payment service called CheckFree lost control of its domain after a DNS record hacking incident. Users were redirected to a site spreading Trojans. That’s irreparable damage for a fintech service.
Domain renewal hijacking
Some attacks capitalize on owner negligence. If a domain isn’t renewed on time, it automatically reverts to the pool of available domains, making it ripe for seizure by anyone, including attackers. For companies, this can result in website downtime and disrupted communication through corporate addresses.
Vulnerabilities in the registrar or DNS providers
Even if you manage your settings perfectly, a weak point may exist with your registrar or DNS host. Hacking these companies’ infrastructure allows attackers to hijack multiple domains en masse.
In 2015, the Vietnamese version of Google, google.vn, was hijacked through an attack on the registrar. Instead of the search engine, visitors were redirected to a page displaying the hackers’ slogans. Though the issue was swiftly resolved, this incident reminded everyone that even Google isn’t immune to hijacking.
Attacks via APIs and Integrations
Many companies use automation tools to manage domains through API keys and CI/CD scripts. If these keys are stored insecurely (for instance, in public repositories), it opens direct access to record management.
What happens after the hijacking
Once an attacker takes control of a domain, they can execute a range of malicious activities. The attackers can:
- Redirect the site to a phishing page.
- Configure mail records (MX) to intercept corporate emails.
- Spoof content and inject malicious code.
- Utilize the brand to send spam or launch further attacks.
Often, victims only discover the hijacking after receiving customer complaints or when their site goes offline. A notable example occurred in 2013 when the so-called “Syrian Electronic Army” group gained access to a registrar account and temporarily redirected the New York Times website to a third-party server. The first reports of the issue came from readers who encountered a fake page instead of the usual content.
What are the consequences of domain hijacking?
Domain hijacking can lead to significant repercussions for companies. Here are the key consequences.
1. Reputational losses
When customers can’t access a website or are redirected to a fraudulent page, trust in the brand rapidly diminishes. Even a brief hijacking can create an impression of unreliability, which is particularly damaging for businesses in the financial, e-commerce, and technology sectors. Rebuilding a tarnished reputation can take months and incur additional costs.
2. Financial damage
Direct losses include website downtime, lost sales, lost leads, and losses from undelivered orders. Indirect losses can accrue from legal fees, PR campaigns aimed at restoring the site’s image, and technical efforts to regain control.
3. Data leakage
If attackers access MX records (mail servers), they can intercept employee communications. This not only opens the door to potential theft of trade secrets and confidential contracts but also compromises customers’ personal data.
4. Use in fraudulent schemes
Hijacked domains may be leveraged by scammers to send spam while impersonating the company, create spoof payment pages to steal card information or distribute malware.
This fraudulent activity can expose the company to lawsuits or fines for violating personal data protection regulations.
5. Legal consequences
Recovering a hijacked domain can take weeks or even months, often requiring communication with the registrar and ICANN, arbitration mechanisms like the UDRP (Uniform Domain-Name Dispute-Resolution Policy), and even national authorities, such as Nominet in the UK.
Even when rights are successfully restored, it doesn’t always mitigate the reputational and financial damages incurred.
How to prevent domain hijacking
1. Choose a reliable registrar
Not all registrars prioritize security. Look for those that offer features like two-factor authentication (2FA), registry lock support, 24/7 customer support, and clear domain recovery processes. A registry lock is a feature that prevents changes to ownership or DNS without manual confirmation.
SpaceLama stands out as an extremely reliable registrar, focused on safety and privacy, making it ideal for businesses concerned about cybersecurity. With a commitment to robust security features like two-factor authentication (2FA) and registry lock support, SpaceLama provides peace of mind for domain owners. Their 24/7 customer support and transparent recovery processes ensure that you’re in safe hands. By choosing SpaceLama, you’re investing in a fortress for your online identity.
2. Enable locks (Registrar Lock / Registry Lock)
- Registrar Lock. Prevents any changes to WHOIS or DNS without logging into your account.
- Registry Lock. This adds another layer of security; even if your account is compromised, the attacker cannot transfer the domain without multiple verifications.
The SSAC report SAC040, “Measures to Protect Registration Services Against Misuse” (2009), emphasizes that registrars should offer additional protection levels, such as lock statuses, to reduce risks.
3. Set up automatic renewal and stay on top of deadlines
Missing renewal dates is a common cause of domain loss, as hijackers often monitor expiring domains. Take these steps:
- enable automatic renewal with your registrar
- link a backup payment method in case your primary card is blocked
- set calendar reminders at least one month before expiration
4. Use two-factor authentication (2FA)
While passwords can be compromised, 2FA (such as using Google Authenticator or even a hardware tool like YubiKey) adds a formidable barrier. Opt for authentication apps instead of SMS, as SMS can be easily intercepted. For essential domains, consider using hardware tokens.
5. Restrict access to credentials
Here’s what we recommend:
- Never share logins and passwords with contractors via email or instant messaging.
- Use password managers (1Password, Bitwarden, KeePass).
- Delegate access through registrar roles (if available), rather than through a shared account.
6. Hide your domain owner’s data (WHOIS privacy)
Open WHOIS data allows attackers to discover the owner’s email address, making phishing attempts easier. Enable WHOIS Privacy Protection, which many registrars offer free of charge.
7. Enable DNSSEC
DNSSEC (Domain Name System Security Extensions) helps protect against DNS record spoofing. When DNSSEC is active, if an attacker attempts to spoof the DNS response, users will see an error instead of a fraudulent website.
Major registrars and DNS providers, like Cloudflare and Google, support one-click activation for DNSSEC.
8. Monitoring and alerts
Here’s what you need to do:
- Set up automatic notifications for DNS record changes.
- Use third-party services (e.g., SecurityTrails, Cloudflare Radar) for monitoring.
- Conduct manual checks at least once a month to ensure A, MX, and CNAME records match your settings.
9. Employee training
Phishing remains the leading vector for attacks. If even one employee falls for a phishing email, such as one claiming “Your account will be deleted, confirm your password”, it could lead to domain access loss. Regular phishing tests and training sessions are essential.
10. Backup plan and documentation
Maintain a detailed list of all domains along with the names of the people responsible for each. Ensure that access data is stored in an offline backup, preferably in an encrypted format. Additionally, develop a step-by-step plan that outlines the necessary actions and contacts to engage in the event of a hijacking incident. Sounds paranoid? A little bit, yes. But with domain hijacking it’s better to be safe than sorry.
What to do if your domain has already been hijacked
If your domain has been hijacked, taking swift action is critical, as every minute counts in mitigating potential damage. The theft of your domain can lead to significant reputational and financial harm, making it vital to act quickly and decisively. A hijacking can disrupt your business operations, compromise customer trust, and expose sensitive information. By following the steps outlined below, you can regain control over your domain and address the immediate threats posed by the hijacker. Time is of the essence; the sooner you can take action, the better your chances of minimizing the impact.
1. Contact your registrar immediately
Reach out to your registrar’s support team through phone or emergency channels. Avoid using email, as your email account may already be compromised. Provide proof of ownership, such as payment transaction details, copies of contracts, or screenshots of your control panel. Request that all changes to the domain be frozen until the situation is clarified.
2. Determine what exactly happened
- Check WHOIS. Look for any changes to the owner or registrar information.
- Check for transfers. Verify whether the domain has been transferred to a different registrar, a common tactic used by attackers.
- Review DNS records. Inspect A, MX, and CNAME records, as hijacking may begin with subtle email redirects.
3. File a complaint with ICANN or your domain registry.
If your domain has been transferred, utilize ICANN’s Transfer Dispute Resolution Policy (TDRP). For international domains (.com, .org, .net), use the Uniform Domain-Name Dispute-Resolution Policy (UDRP). Keep in mind that national domains (.fr, .kr, etc.) have their own specific mechanisms, typically managed through local regulators.
4. Involve law enforcement
File a report with cyber police (yes, there’s “internet cops” now, wild) or the appropriate agency, such as CERT. Preserve all evidence, including phishing emails, login logs, and transaction records. In some countries, these cases are classified as cybercrimes, which can accelerate the investigation.
5. Notify clients and users
If the hijacking includes website or email spoofing, alert your clients as soon as possible to prevent them from falling for scams. Use alternative channels to communicate, such as social media, mailings from backup domains, and instant messaging apps.
6. Engage legal counsel
Legal advice can be crucial, especially if the domain serves commercial purposes. Companies often turn to arbitration and lawsuits if negotiations through ICANN or the registrar fail.
7. Conduct an internal audit
Once you regain the domain, it’s essential to understand how the theft occurred. Investigate whether it was due to phishing, a password leak, or employee error (unless it’s your CEO, in which case you should find somebody else to blame instead). Identifying the root cause can help you implement stronger security measures moving forward.
Domain names are a company’s digital real estate. Protecting them requires the same level of attention as safeguarding financial assets or intellectual property. The stories of the New York Times, Google, and other major players illustrate that even established brands can lose control of their domains if they overlook basic security measures.
The bottom line is straightforward: prevention is far cheaper than dealing with a crisis. And implementing safeguards like a registry lock, two-factor authentication (2FA), transferring your domain to SpaceLama and setting up auto-renewal typically costs only a few tens of dollars per year. In contrast, the financial and reputational losses from domain theft can reach into the hundreds of thousands and consume years of effort to restore a brand’s image.